Security Control Audit (SCA) Service
Continuous Security Validation Managed Service for Cyber-Threat Simulation & Mitigation
Les solutions d’automatisation et d’orchestration ne sont pas qu’à l’usage du monde de la Cyber Défense ; en effet, vos adversaires (hackers) vous attaquent constamment à l’aide d’outils automatisés (scanner de vulnérabilités, scanners de ports, …)
Leur objectif primaire est simple : tester en masse les failles et vulnérabilités exploitables des services exposés sur Internet. Prenons exemples des quelques « Common Vulnerabilities and Exposures » (CVE) qui ont récemment faites parler d’elles :
- CVE-2020-5902 | Multiples vulnérabilités dans F5 BIG-IP TMUI
- CVE-2019-19781 | Vulnérabilité dans Citrix Application Delivery Controller et Gateway
- CVE-2018-13379 | Multiples vulnérabilités dans Fortinet FortiOS
- CVE-2020-0609 | Multiples vulnérabilités dans le serveur de passerelle RDP de Windows
Premièrement, saviez-vous que vos équipements de contrôle de sécurité (Fortinet, Citrix, F5 …) avaient une ou plusieurs vulnérabilités rendues publiques, et dont la protection pour laquelle vous avez investi de l’argent et du temps de configuration pouvait s’en trouver compromise ?
Enfin, comme les menaces avancées combinent des techniques sophistiquées et introduisent constamment de nouvelles variantes pour échapper aux défenses, comment vous assurez-vous que votre organisation résistera au dernier scénario d’attaque avancé (cf MITRE ATT&CK Framework) ?
Pour faire face à un grand nombre de menaces en évolution rapide, il faut donc une nouvelle approche de la validation des contrôles de sécurité en place pour s’assurer de l’efficacité de leur protection.
e-Xpert Solutions SA met donc à disposition son nouveau service de sécurité managé « Security Control Audit » (SCA), bâtit sur l’expertise des analystes de sécurité du SoC « AT-Defense » et la solution « Continuous Adversary Simulation Platform » de PICUS Security.
Comment fonctionne le service ?
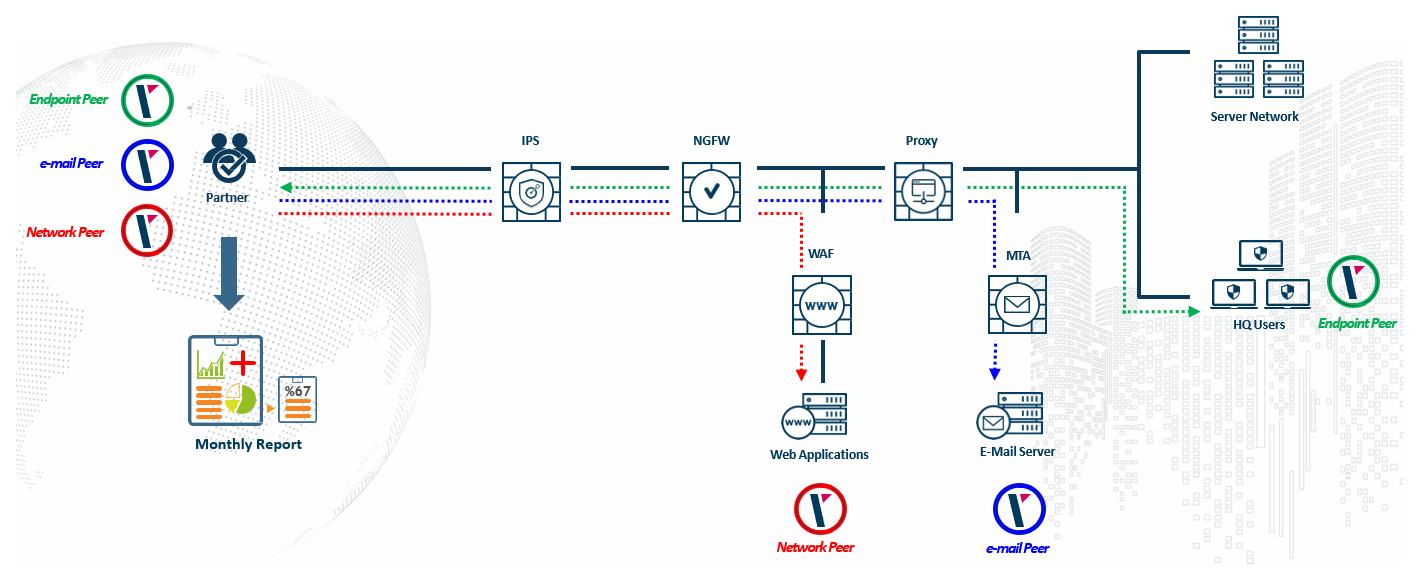
Contrairement aux scanners de vulnérabilités, la plate-forme lance des cyber-attaques en simulant à la fois les systèmes victimes et attaquants au sein des réseaux de production. Cela permet d’évaluer en permanence l’efficacité de la configuration des contrôles de sécurité, sans nuire aux applications métier.
Trois sondes victimes sont incluses dans le service de base:
Network
Pour attaquer la sonde victime (de couleur rouge) hébergée dans la DMZ, l’attaque passera par exemple au travers d’un pare-feu d’application Web (WAF), IPS, proxy … L’objectif est ici de tester si le WAF stoppe bien les attaques à destination des services publiés sur Internet et hébergés dans la DMZ.
la sonde e-mail va utiliser une boite aux lettre email générique. Cette mailbox e est en générale protégée par à une solution de sécurité de messagerie (MTA). Cette sonde recevra des e-mails contenant des pièces-jointes malicieuses ainsi que des liens d’attaque de phishing. L’objectif est de tester ici si le contrôle de sécurité MTA bloque bien ces attaques. EndPoint: la sonde EndPoint dit être installée sur un poste de travail type de l’entreprise sous la forme d’un agent léger. Elle va tenter de récupérer du contenu malicieux au travers de votre Proxy Web et/ou Firewall Next Generation avec IPS et ou Sandboxing. Le premier but ici est de tester l’efficacité du contrôle de sécurité Proxy Web et ou NGFW à bloquer les contenus malicieux. Si un contenu malicieux venait à descendre sur le poste de travail, alors le second but est de tester si la solution de sécurité embarqué sur le poste de travail (ex : NG Antvirus) permet de réellement de stopper l’attaque au moment de son exécution.
e
est en générale protégée par à une solution de sécurité de messagerie (MTA). Cette sonde recevra des e-mails contenant des pièces-jointes malicieuses ainsi que des liens d’attaque de phishing. L’objectif est de tester ici si le contrôle de sécurité MTA bloque bien ces attaques.
EndPoint
la sonde EndPoint dit être installée sur un poste de travail type de l’entreprise sous la forme d’un agent léger. Elle va tenter de récupérer du contenu malicieux au travers de votre Proxy Web et/ou Firewall Next Generation avec IPS et ou Sandboxing. Le premier but ici est de tester l’efficacité du contrôle de sécurité Proxy Web et ou NGFW à bloquer les contenus malicieux. Si un contenu malicieux venait à descendre sur le poste de travail, alors le second but est de tester si la solution de sécurité embarqué sur le poste de travail (ex : NG Antvirus) permet de réellement de stopper l’attaque au moment de son exécution.
Si l’élément de control de sécurité (WAF, NGFW, NG Antivirus, MTA) ne bloque pas l’attaque, c’est la preuve qu’il faut apporter des adaptations pour remédier à la faiblesse du control de sécurité. e-Xpert Solutions fournira donc un rapport détaillé de la posture de sécurité de chacun des élément contrôlés, accompagné des recommandations d’atténuation dans le cadre du reporting.
Les fonctionnalités du service SCA
- Tester automatiquement et en continue 24/7 la résilience de votre infrastructure de sécurité, comme le font actuellement les Cyber Criminels les plus avancés.
- Evaluer les capacités de contrôle de sécurité existants vis-à-vis des dernières menaces existantes et émergeantes.
- Adapter la mitigation avec précision pour chacun des échantillons de menace.
- Identifiez les risques de sécurité grâce à une analyse détaillée de vos rapports de posture de sécurité.
Les avantages du service SCA
- Quelle est l’efficacité réelle des contrôles de sécurité en place face aux menaces existantes ?
- Quelles actions doivent être entreprises en priorité par les équipes pour optimiser l’efficacité des contrôles de sécurité en place ?
- Quels sont les choix d’investissements les plus efficients à maintenir ou à développer pour augmenter concrètement le niveau de sécurité ?
e-Xpert Solution a développé deux offres : l’une permet de réaliser un audit ponctuel une à plusieurs fois par année, l’autre de bénéficier d’un service mensuel récurent avec un alerting hebdomadaire en cas d’anomalies détectées. Par exemple, lorsqu’un changement aurait impliqué une diminution des indicateurs de niveau de sécurité.
